Archer IRM Integration
How to configure the integration between Secberus and Archer IRM.
Overview
Secberus can add policy and policy violation data directly into an Archer instance. The corresponding elements within Archer are known as Configuration Checks and Configuration Check Results. These items can be found in the Archer instance under the IT Controls Assurance heading.
Setup
Prerequisites
Before you begin, make sure you have the following items.
- Permissions within Secberus to create an integration.
- The following information about your Archer instance:
- Archer hostname or IP address and port number
- Archer username & password that can access the Archer REST API
- Archer instance name
Configuration
To connect Secberus to your Archer instance, from within the Secberus application, browse to Settings -> Integrations in the menu.
On the Integrations page you will see the list of available integrations at the top. Click on the "Archer" tile. This will bring up a form where you will input the prerequisite data items about your Archer instance.
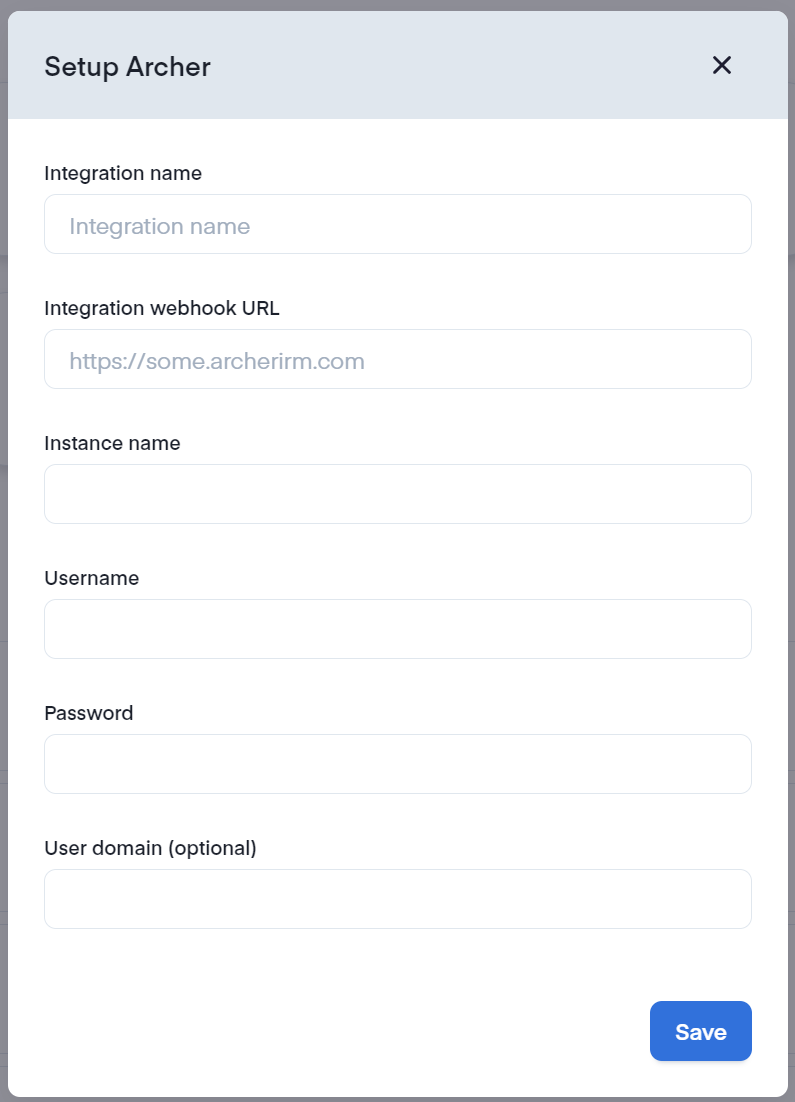
Once the form is submitted, the integration configuration is complete. You may now use the Archer integration as a target for one or more Secberus Workflows so Secberus will automatically populate your Archer instance with policy violations.
Updated 9 months ago