Authentication
How to set up SSO authentication using an Okta integration. You can follow these steps to configure OIDC Authentication using a different provider as they will be similar.
You can configure the Secberus platform for single sign-on through Okta. Here are the steps.
- Log into your Okta account
- Select Applications page
- Click Create App Integration
- Select OIDC - OpenID Connect as the Sign-in method
- In Application type, select Web Application
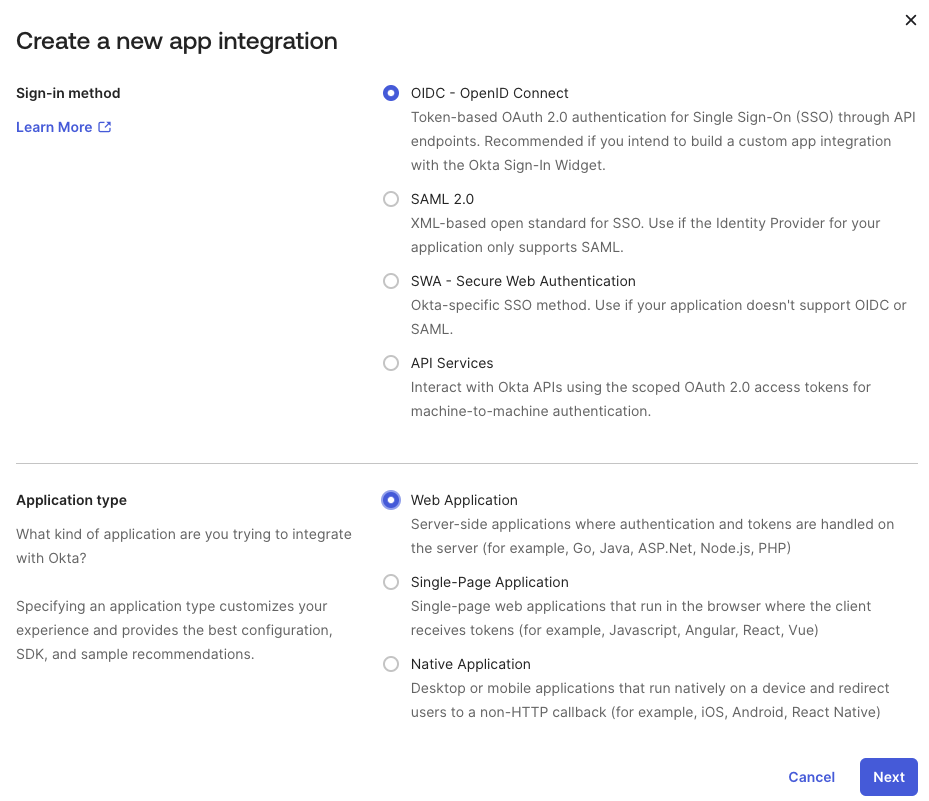
- Click Next
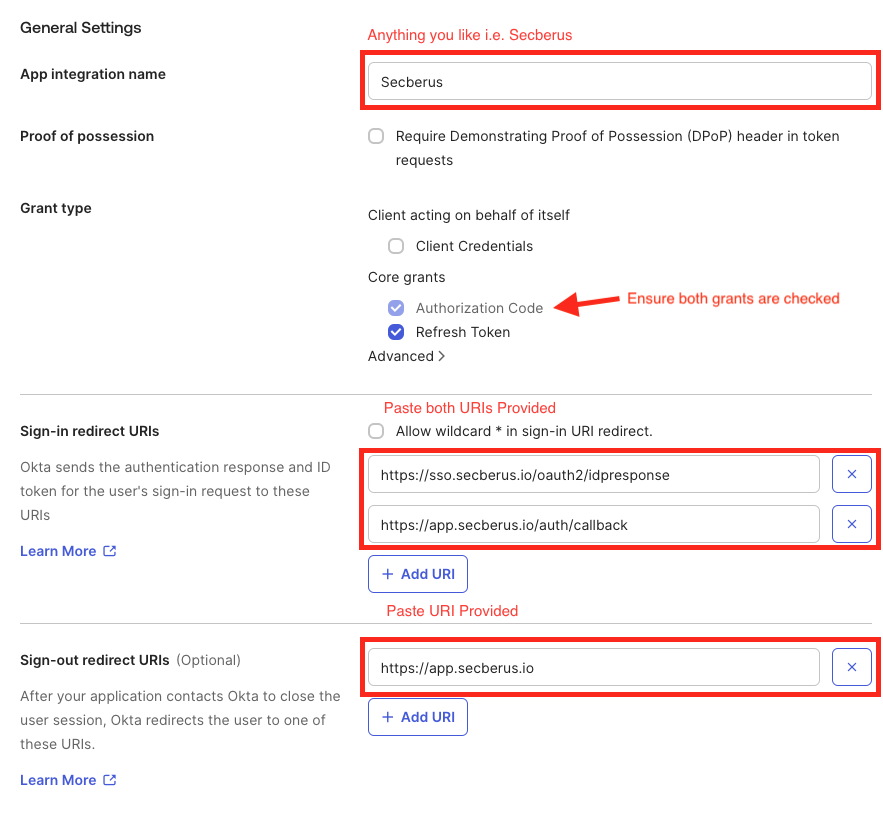
- Configure Application:
- Name your application anything you like, i.e. Secberus
- Ensure that Authorization Code and Refresh Token code grants are checked
- In Sign-in redirect URIs, provide the following URIs:
https://sso.secberus.io/oauth2/idpresponsehttps://app.secberus.io/auth/callback
- In Sign-out redirect URIs, provide the following URI:
https://app.secberus.io
- Assign group access to the groups you want to be able to sign into Secberus using your app integration.
- Click Save.
- You will be provided a Client ID and a Client Secret. Be sure to save these values somewhere safe since you will need to provide this information when you add your provider in Secberus. This will be the only time the Client Secret will be shown.
- You will also need to provide Secberus the issuer_url. In your Okta application, within the Sign-on tab, under OpenID Connect ID Token, ensure that the Issuer is set to Okta URL (
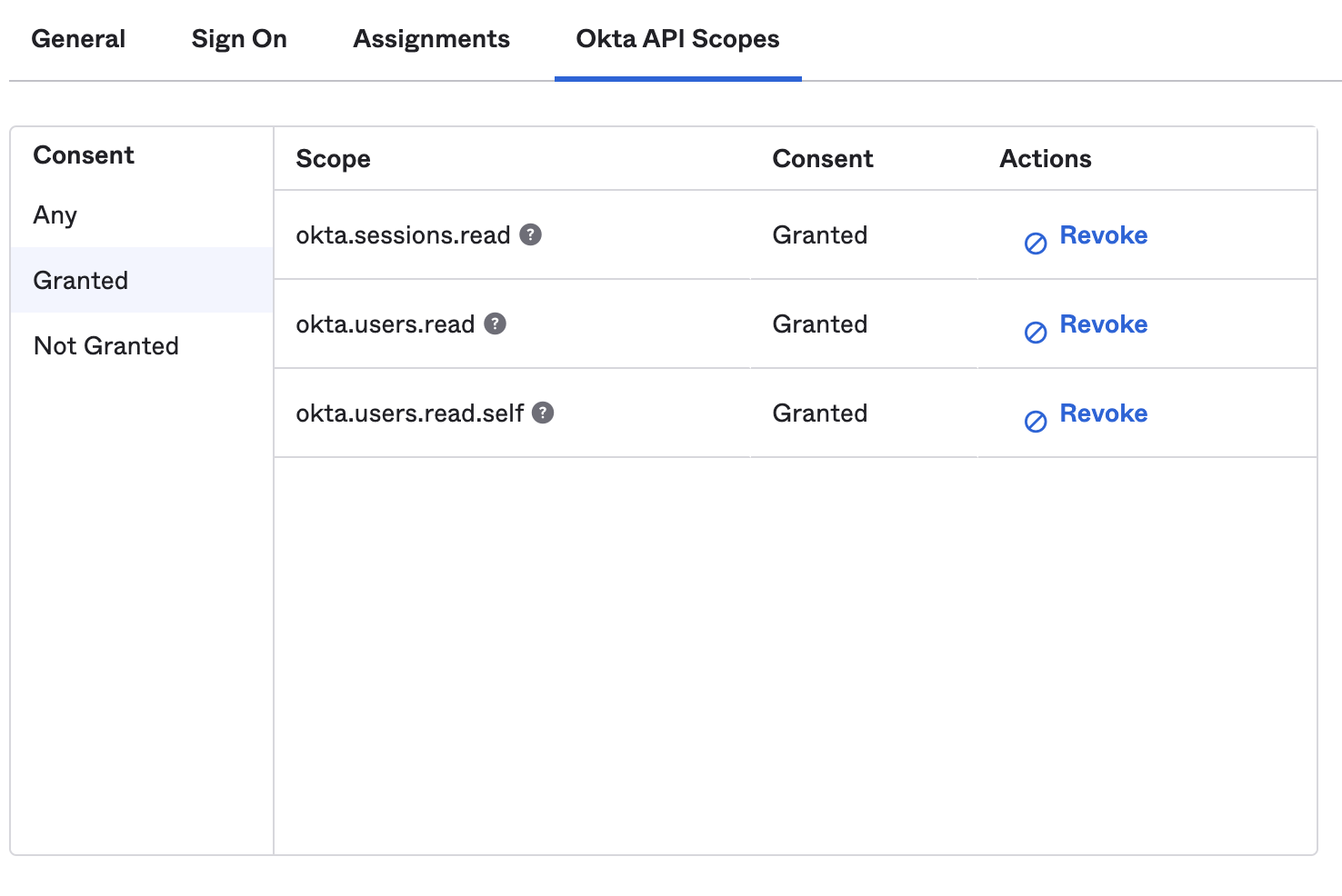
https://example-12345.okta.com). - Finally, update the app's API Scopes to grant:
- sessions.read,
- users.read, and
- users.read.self
- In the Secberus dashboard, when adding your SSO provider in the Manage account admin panel > Authentication screen. Provide
- Provider name, i.e.
okta - Domain - users who sign-in to
app.secberus.iowith the provided domain will be redirected to your SSO provider - Provider Type:
OpenID Connect (OIDC) - Client ID, Client Secret, and Issuer URL from steps 8 and 9.
- Attribute mappings. There are mandatory claims that are required to sign-in. For OIDC, the usual values in the claims are listed below. If these are configured differently in your SSO provider, please provide those values instead.
- First Name:
given_name - Last Name:
family_name - Email:
email
- First Name:
- Provider name, i.e.
Your Okta integration configuration is now complete.
Updated about 1 month ago