AWS IAM Role
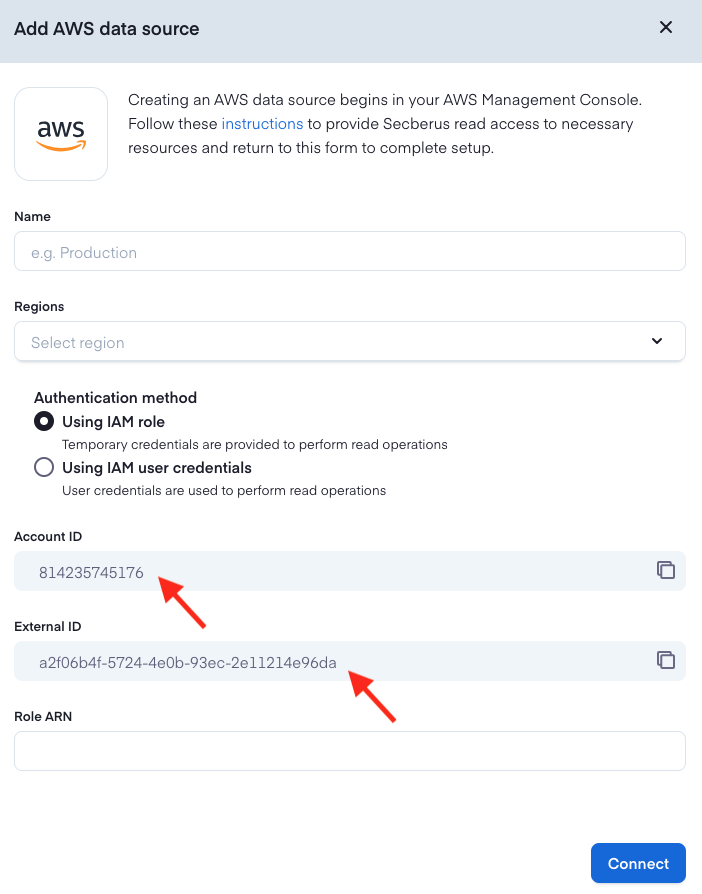
Secberus AWS account and External ID
When creating the AWS IAM role, you will allow the Secberus AWS account access to use your role. For added security, each AWS data source connection in Secberus uses a unique external ID. The external ID is generated and provided for you when you attempt to create a AWS data source connection.
- Log into Secberus and select the org you want to create the datasource connection in.
- Click on Settings and then click on Data sources.
- Choose the AWS data source type in the Add new data source section.
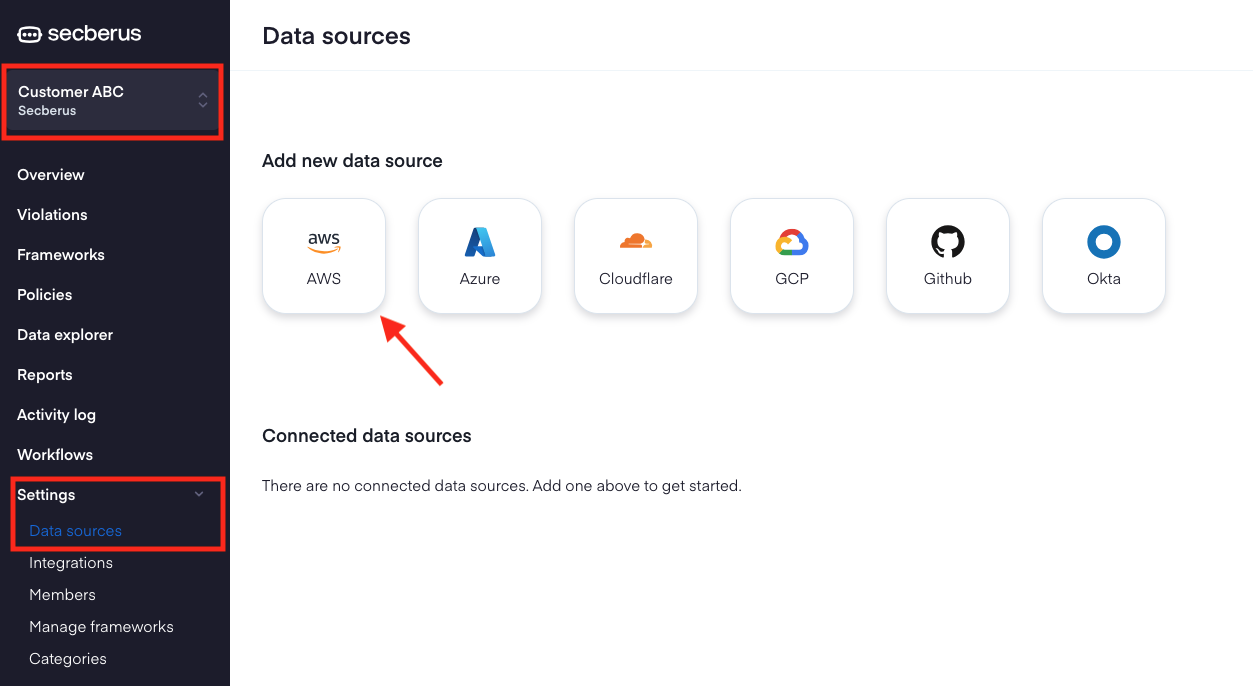
- Take note of the Secberus AWS account ID and your unique external ID.
Create AWS policy using AWS Console
We need to create an AWS policy that provides the required permissions for Secberus to collect your AWS account data.
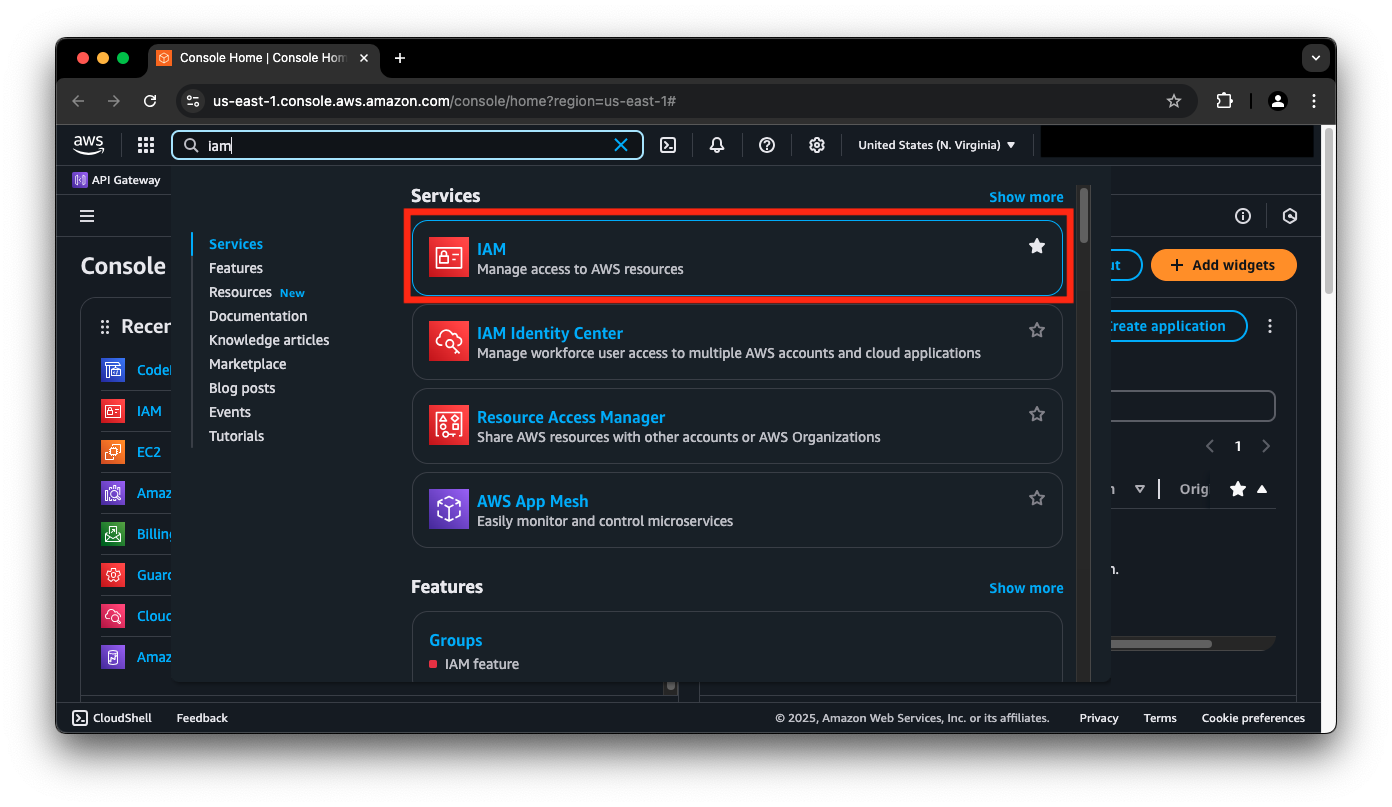
- In the AWS console, use the Search bar to navigate to the IAM dashboard within the AWS Management Console. Type IAM and click on the IAM service.
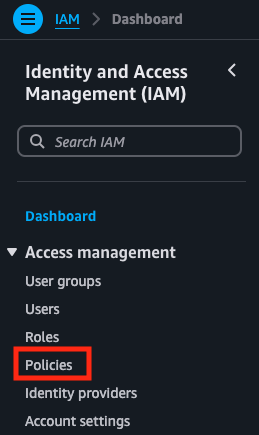
- From the IAM dashboard, in the left-hand navigation bar, under Access management, select Policies.
- Click Create policy.
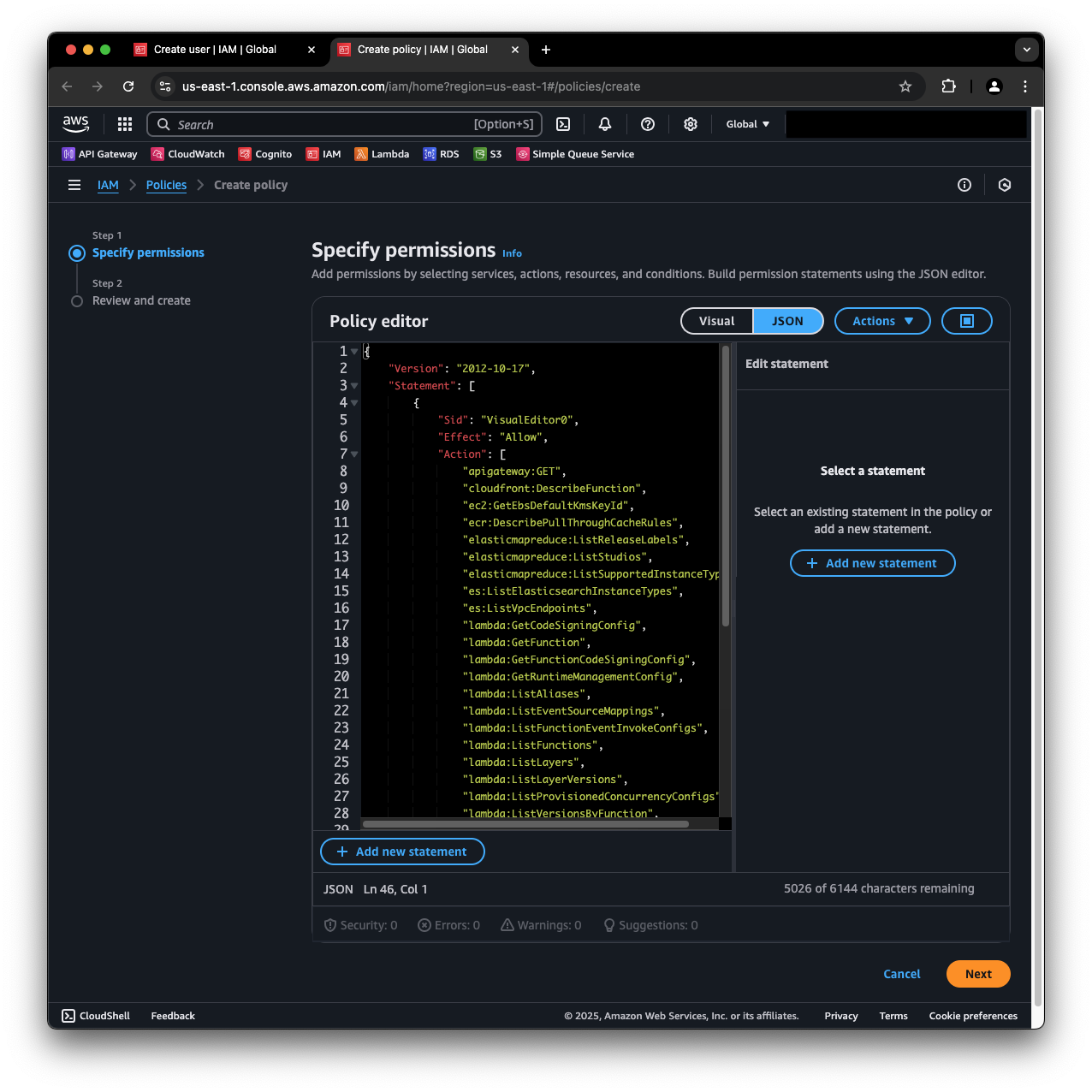
- In the Specify permissions screen, within the Policy editor, click on JSON. Copy the following JSON policy and paste it in the editor.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"apigateway:GET",
"cloudfront:DescribeFunction",
"ec2:GetEbsDefaultKmsKeyId",
"ecr:DescribePullThroughCacheRules",
"elasticmapreduce:ListReleaseLabels",
"elasticmapreduce:ListStudios",
"elasticmapreduce:ListSupportedInstanceTypes",
"es:ListElasticsearchInstanceTypes",
"es:ListVpcEndpoints",
"lambda:GetCodeSigningConfig",
"lambda:GetFunction",
"lambda:GetFunctionCodeSigningConfig",
"lambda:GetRuntimeManagementConfig",
"lambda:ListAliases",
"lambda:ListEventSourceMappings",
"lambda:ListFunctionEventInvokeConfigs",
"lambda:ListFunctions",
"lambda:ListLayers",
"lambda:ListLayerVersions",
"lambda:ListProvisionedConcurrencyConfigs",
"lambda:ListVersionsByFunction",
"organizations:ListAccounts",
"organizations:ListRoots",
"organizations:ListPolicies",
"organizations:ListDelegatedAdministrators",
"s3:ListBucket",
"sns:GetSubscriptionAttributes",
"waf:ListRuleGroups",
"waf:ListRules",
"waf:ListSubscribedRuleGroups",
"waf-regional:ListRateBasedRules",
"waf-regional:ListRuleGroups",
"waf-regional:ListRules",
"wafv2:DescribeManagedRuleGroup"
],
"Resource": "*"
}
]
}
- Click Next.
- In the Review and create screen, give the policy a meaningful name and click on Create policy.
Creating an IAM Role
- From the IAM dashboard, in the left-hand navigation bar, under Access management, select Roles.
- Create a role by clicking on with Create role
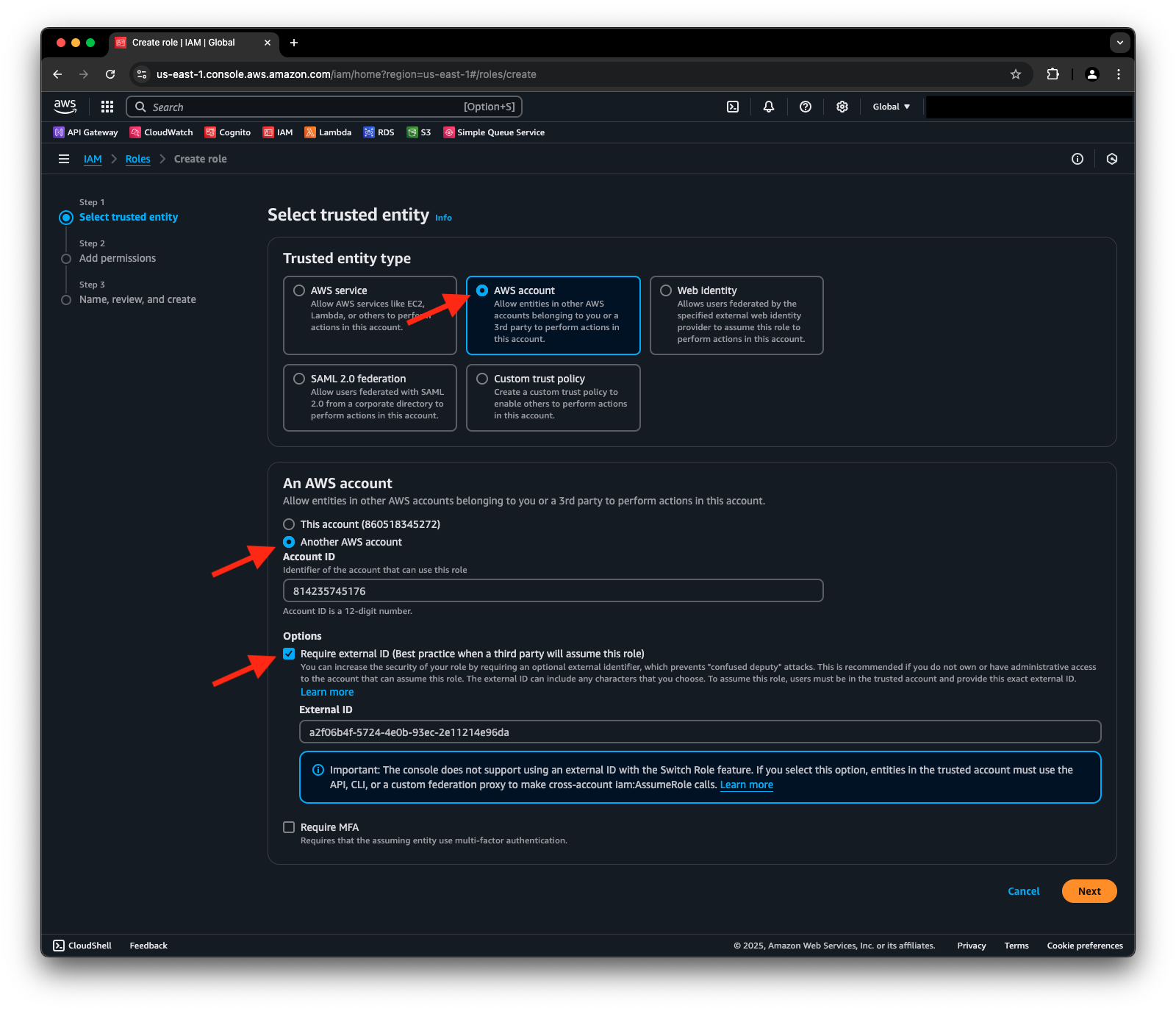
- In the Specify trusted entity screen, in Trusted entity type, select AWS account.
- In An AWS account, select Another AWS account. Type in the Secberus AWS account ID 814235745176.
- Under Options, check Require external ID (Best practice when a third party will assume this role). Enter the external ID generated for your data source from step 4 in the Secberus AWS account and External ID section.
- Click Next.
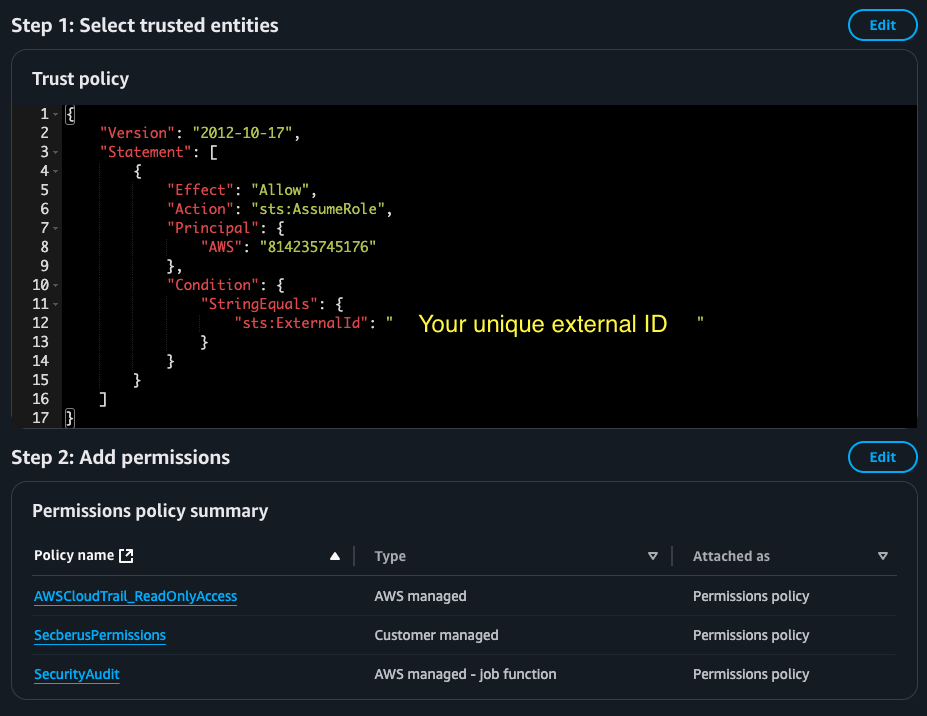
- In the Add permissions screen, under Permission policies, search for and select the following policies:
- SecurityAudit,
- AWSCloudTrail_ReadOnlyAccess, and
- the policy created in step 9 of the Create AWS policy using AWS Console section
- Click Next.
- In the Name, review, and create screen, provide a meaningful role name and verify the trusted entity and permissions are correct.
- Once verified, click Create Role.
- Search for and click on the role you just created.
- Take note of the role's ARN.
Secberus - Connect AWS Datasource using IAM Role
- Log into Secberus and select the org you want to create the datasource connection in.
- Click on Settings and then click on Data sources.
- Choose the AWS data source type in the Add new data source section.

- Populate the Name field, select the appropriate Regions, and choose Using IAM role as the Authentication method. Then enter the ARN of the IAM role you created in the previous section.
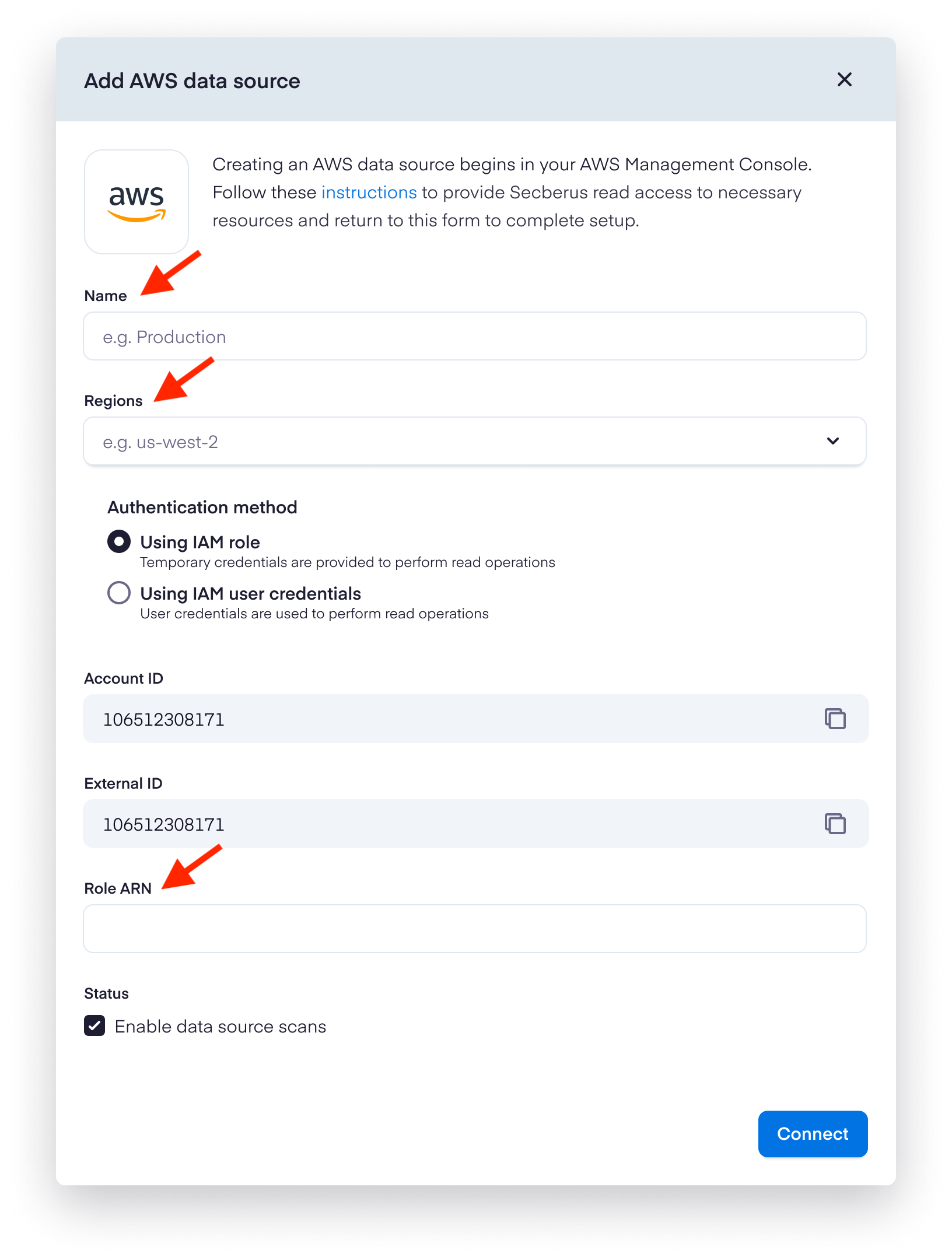
- With the credentials in place, set the desired status to enable data source scans, and click the Connect button to initialize your data source.
CONGRATULATIONS 🎉You successfully onboarded an AWS account. You can add more AWS accounts, onboard other cloud provider accounts, or apply a policy to this AWS account. Additionally, you can view the connection status once Secberus begins collecting resource data for evaluation.
Updated 9 months ago
What’s Next