AWS IAM User
Creating an IAM User using the AWS Console
- In the AWS console, use the Search bar to navigate to the IAM dashboard within the AWS Management Console. Type IAM and click on the IAM service.
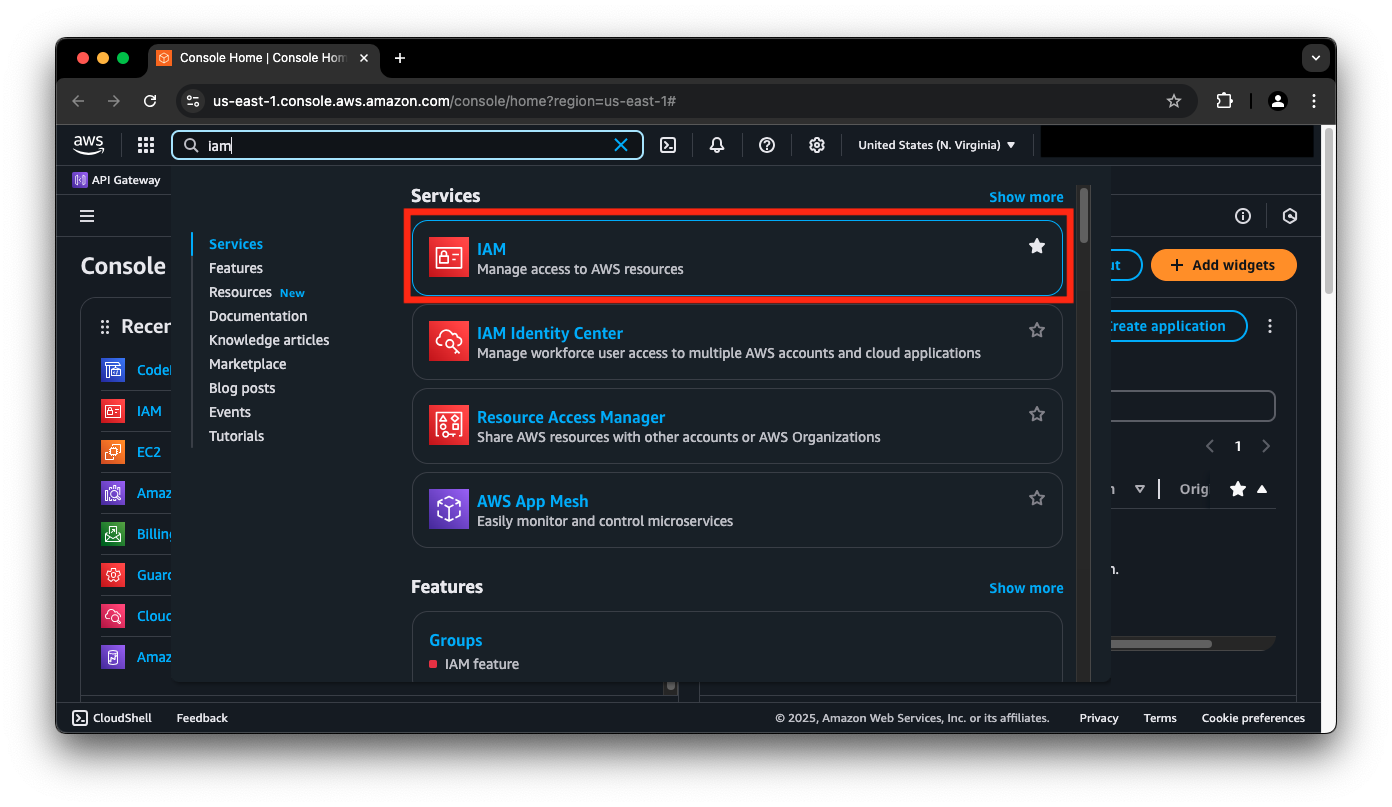
- From the IAM dashboard, in the left-hand navigation bar, under Access management, select Users.
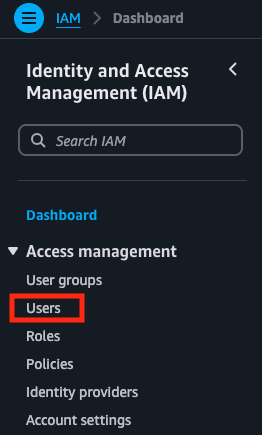
- Create a user with Create user.
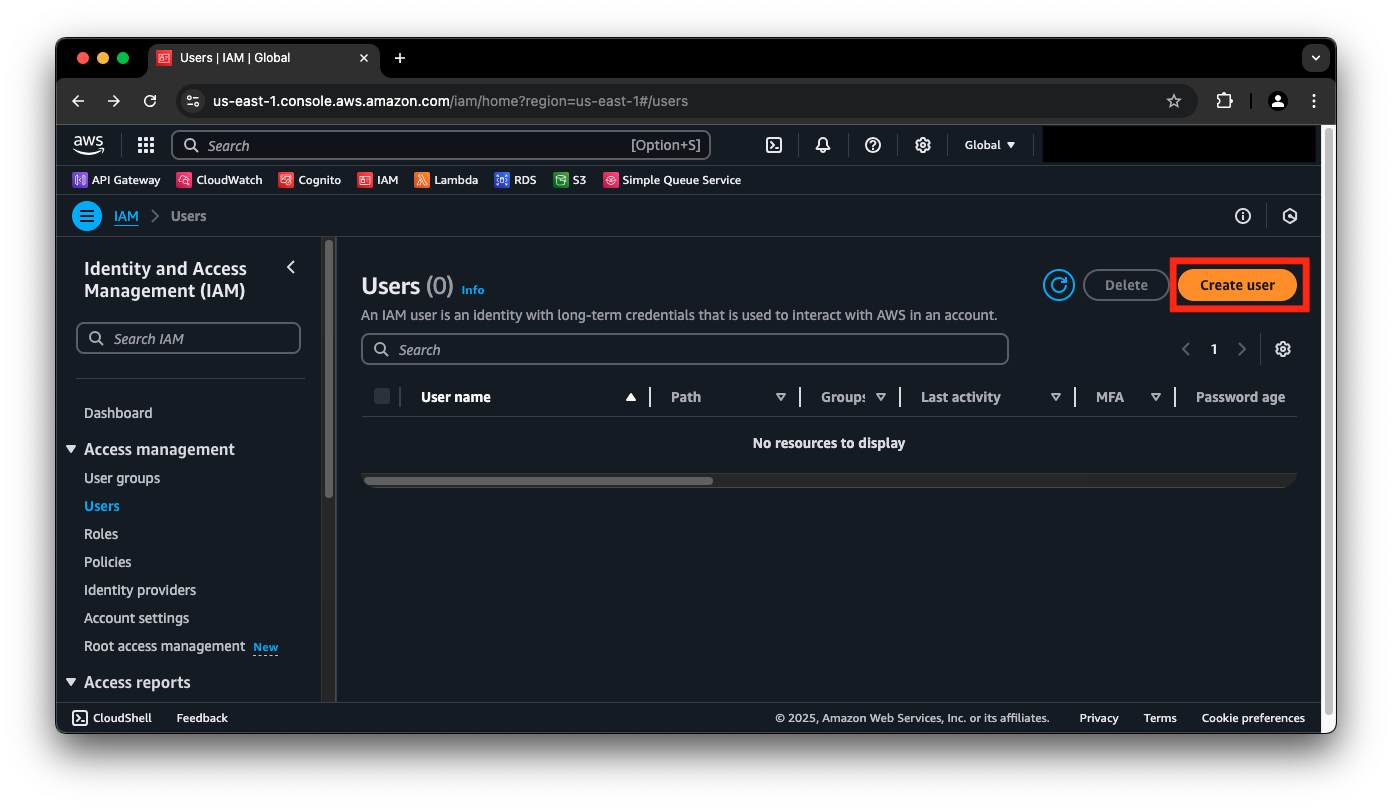
- In the Specify user details screen, give the user a meaningful name. Secberus will use this user's access key, there is no need provide console access to this user. Click Next.
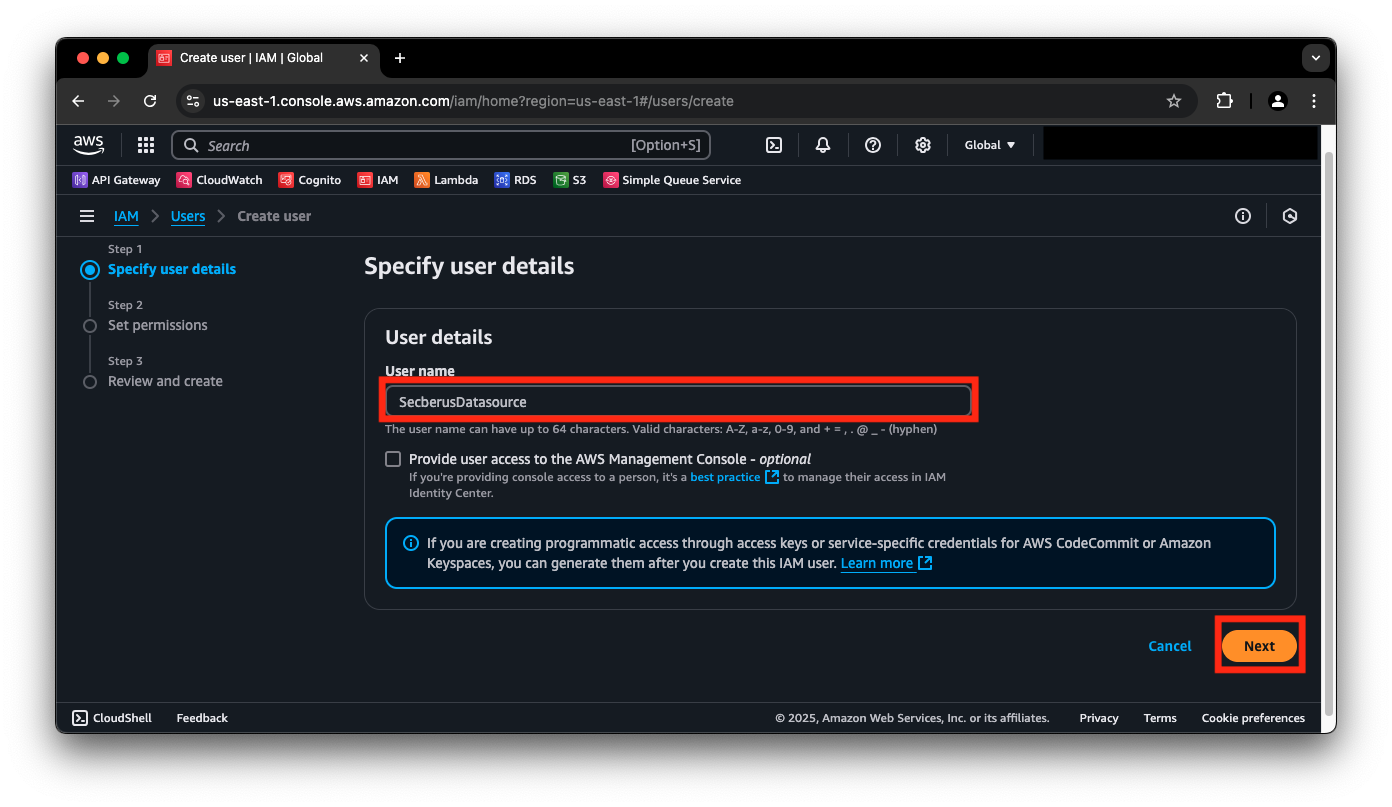
- In the Set permissions screen, under Permission options select the Attach policies directly option.
- Under Permission policies, click Create policy. This will open a new window.
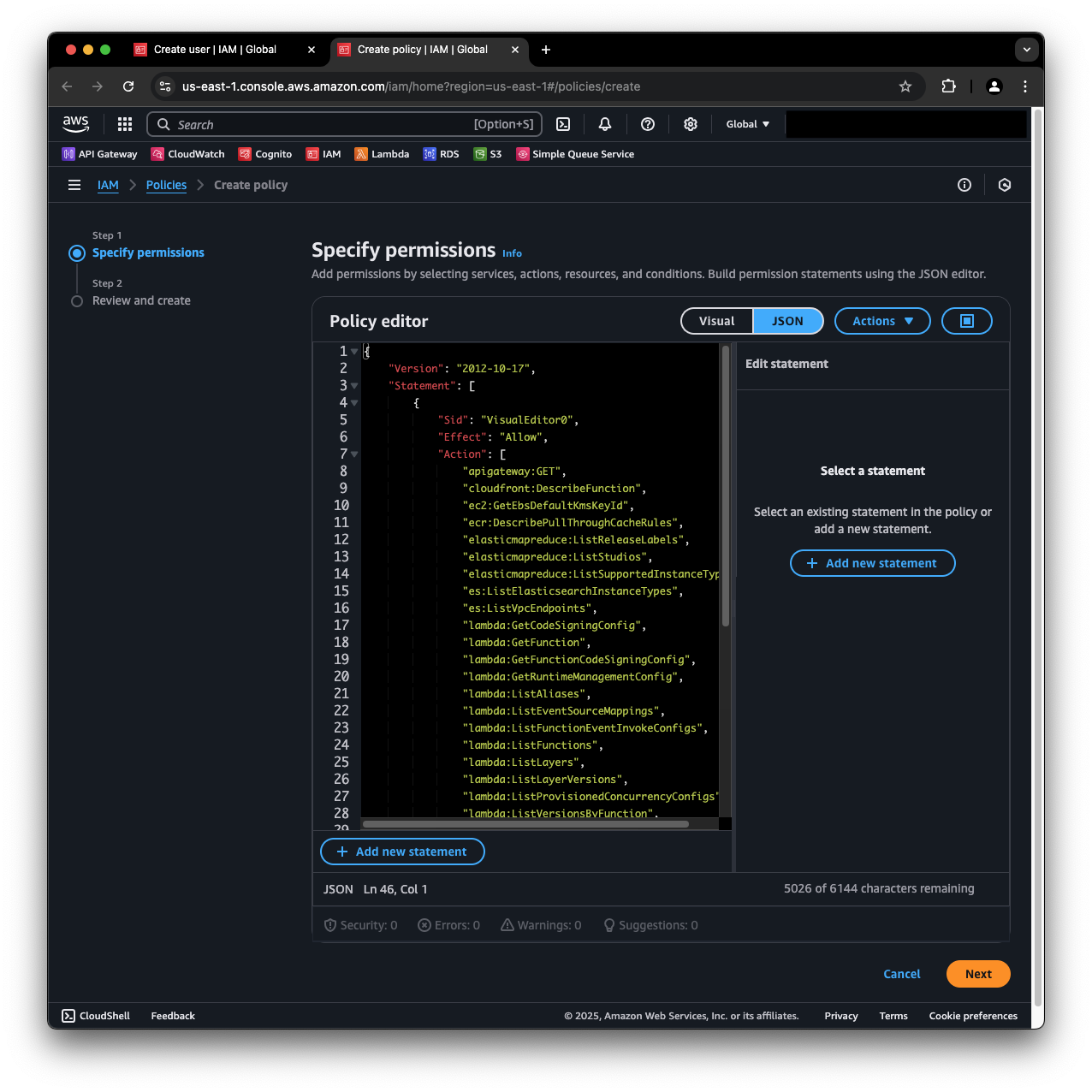
- In the Specify permissions screen, within the Policy editor, click on JSON. Copy the following JSON policy and paste it in the editor.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"apigateway:GET",
"cloudfront:DescribeFunction",
"ec2:GetEbsDefaultKmsKeyId",
"ecr:DescribePullThroughCacheRules",
"elasticmapreduce:ListReleaseLabels",
"elasticmapreduce:ListStudios",
"elasticmapreduce:ListSupportedInstanceTypes",
"es:ListElasticsearchInstanceTypes",
"es:ListVpcEndpoints",
"lambda:GetCodeSigningConfig",
"lambda:GetFunction",
"lambda:GetFunctionCodeSigningConfig",
"lambda:GetRuntimeManagementConfig",
"lambda:ListAliases",
"lambda:ListEventSourceMappings",
"lambda:ListFunctionEventInvokeConfigs",
"lambda:ListFunctions",
"lambda:ListLayers",
"lambda:ListLayerVersions",
"lambda:ListProvisionedConcurrencyConfigs",
"lambda:ListVersionsByFunction",
"organizations:ListAccounts",
"organizations:ListRoots",
"organizations:ListPolicies",
"organizations:ListDelegatedAdministrators",
"s3:ListBucket",
"sns:GetSubscriptionAttributes",
"waf:ListRuleGroups",
"waf:ListRules",
"waf:ListSubscribedRuleGroups",
"waf-regional:ListRateBasedRules",
"waf-regional:ListRuleGroups",
"waf-regional:ListRules",
"wafv2:DescribeManagedRuleGroup"
],
"Resource": "*"
}
]
}
- Click Next.
- In the Review and create screen, give the policy a meaningful name and click on Create policy.
- Once the policy is created, go back to the Create user tab. Within Permission policies, click on refresh so the newly created policy will show up in the list.
- Search for and select the following policies:
- SecurityAudit,
- AWSCloudTrail_ReadOnlyAccess, and
- the policy created in step 6
- Click Next.
- In the Review and create screen, click Create user.
- After the user is created, click on the user. Click on the Security credentials tab and then click Create access key.
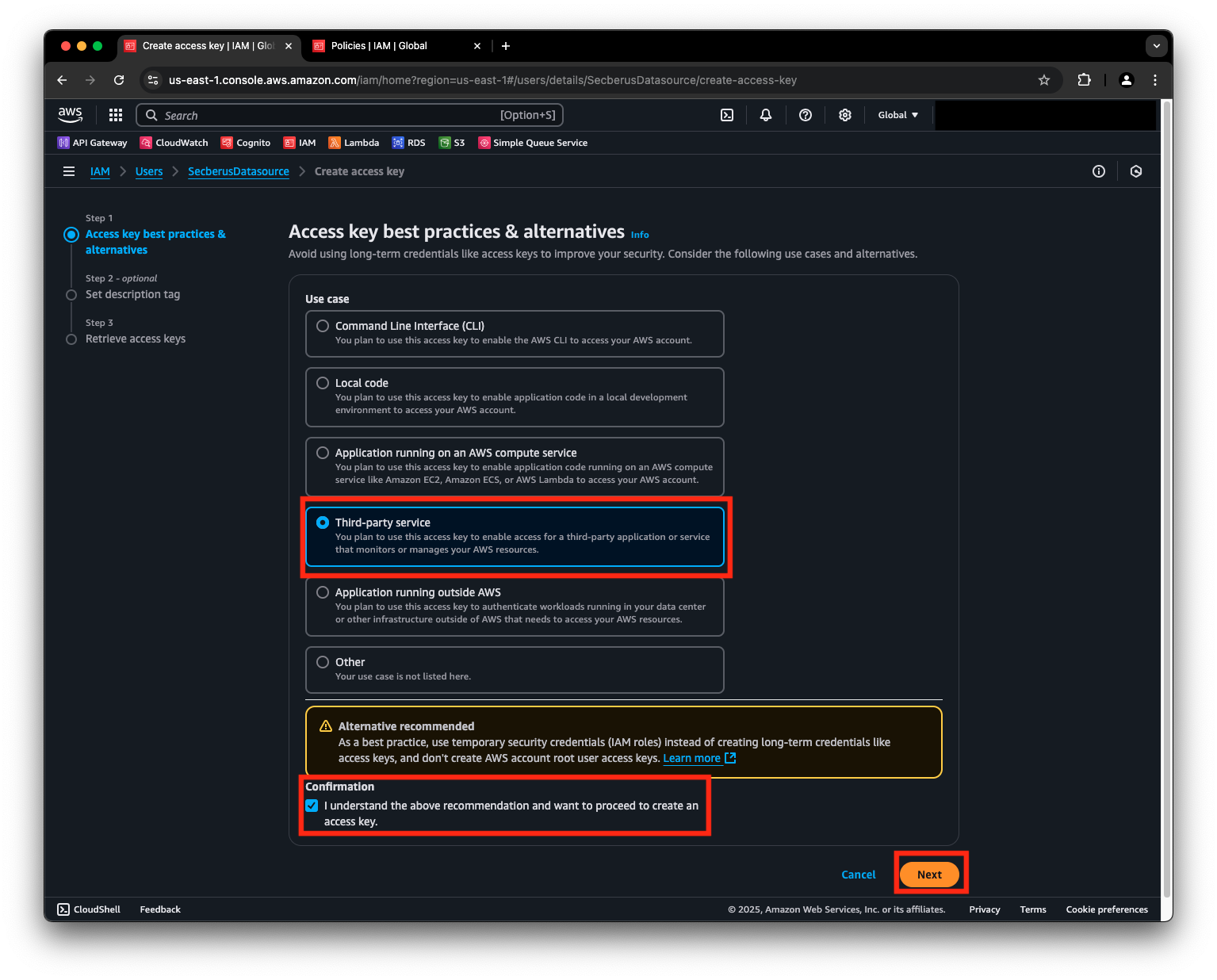
- In the Access key best practices & alternatives screen, select the Third-party service use case. Click on the confirmation check box and click Next.
- Give an optional description, click on Create access key.
- In the Retrieve access keys screen, take note of the Access key and Secret access key. These will be needed when creating the AWS datasource within Secberus.
Secberus - Connect AWS Datasource
- Log into Secberus and select the org you want to create the datasource connection in.
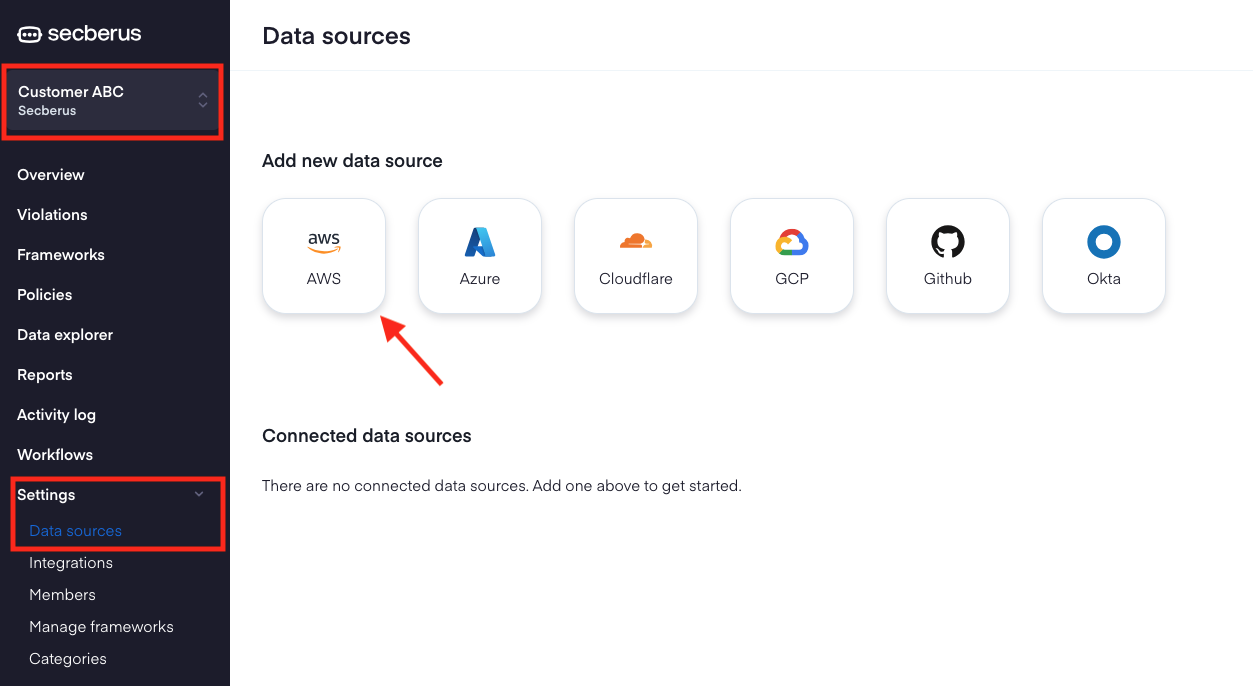
- Click on Settings and then click on Data sources.
- Choose the AWS data source type in the Add new data source section.
- Populate the Name field, select the appropriate Regions, and choose Using IAM user credentials as the Authentication method. Then copy the credentials you saved from step 15 into the Access key ID and Secret access key fields.
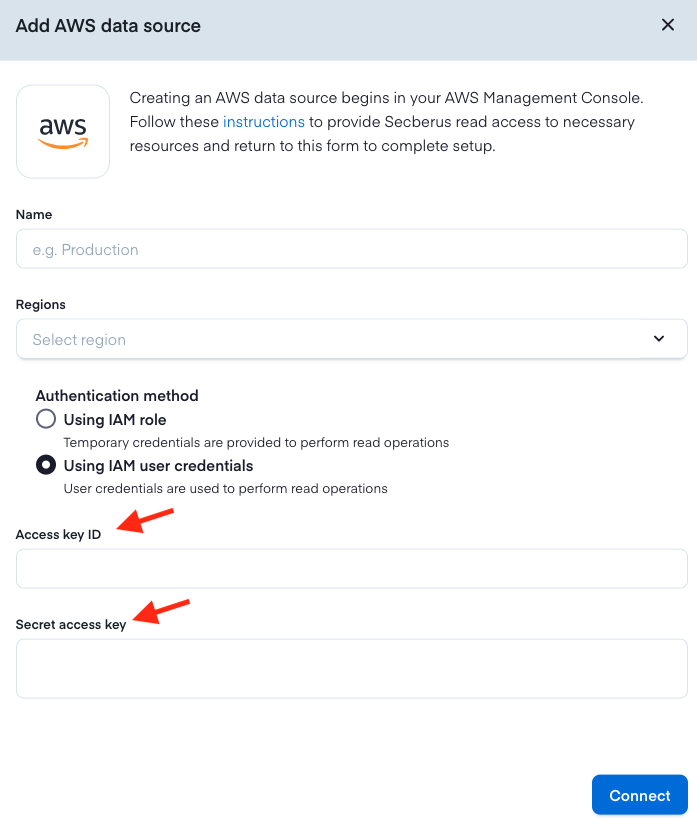
- With the credentials in place, click the Connect button to initialize your data source.
CONGRATULATIONS 🎉You successfully onboarded an AWS account. You can add more AWS accounts, onboard other cloud provider accounts, or apply a policy to this AWS account. Additionally, you can view the connection status once Secberus begins collecting resource data for evaluation.
Updated 9 months ago
What’s Next